Our Blog.
Keep up with the latest news and trends in game development and cybersecurity, including tools, techniques, and industry insights.
All Posts

This article is a deeper dive into how the Cheat Engine works behind the scenes. It builds on the previous article and focuses on more technical depth and what developers should be aware of.

What if your newest hire wasn't who they claimed to be? From AI-generated faces to deepfake interviews, attackers are exploiting remote hiring processes.
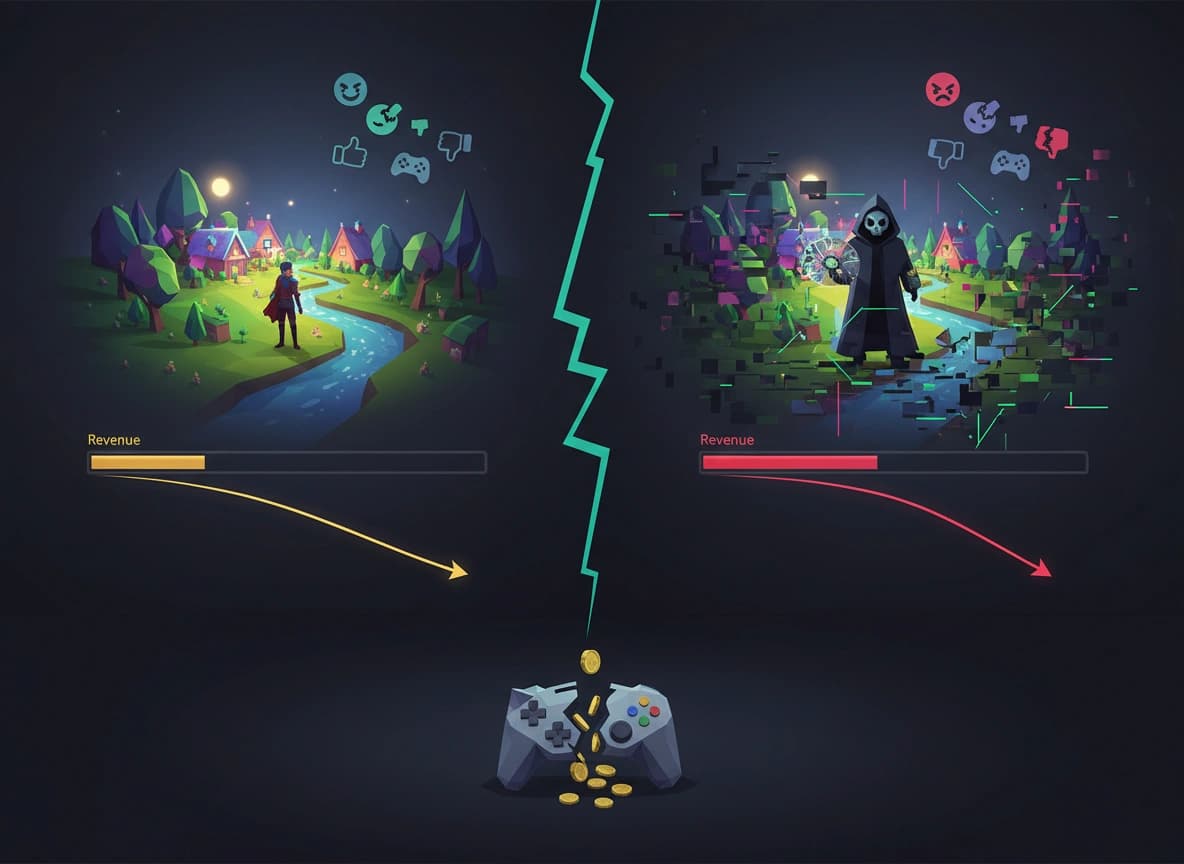
For indie developers, every sale is survival. Here’s how piracy and cheating suffocate that vital revenue.

Learn why antivirus flags your new game, how Windows evaluates unknown apps, and how to build trust.

For the price of a coffee, anyone can now rent a cyber weapon powerful enough to knock your website or your online store offline.

Learn how to automate Unity asset packaging and export in seconds, skipping the editor.